 Recent world events that started as technological glitches or dysfunctions have become major objects of debate in politics, geopolitics and the economy. It is useful to consider geotechnology as a tool which enables key players’ strategic decisions based on geospatial knowledge. However, in the unpredictable game of world situations, geotechnology appears as an independent “natural” player, beyond the control of its makers and dictating new opportunities or able to disrupt the preexisting balance.
Recent world events that started as technological glitches or dysfunctions have become major objects of debate in politics, geopolitics and the economy. It is useful to consider geotechnology as a tool which enables key players’ strategic decisions based on geospatial knowledge. However, in the unpredictable game of world situations, geotechnology appears as an independent “natural” player, beyond the control of its makers and dictating new opportunities or able to disrupt the preexisting balance.
In the news reports that follow, several examples of failures of technological systems indicate both critical shortcomings as well as our current reliance on working infrastructure, which silently makes up a world system functioning at all times.
Are world events driven by geotechnologies? If they were, a technical perspective would offer a key handle on all ongoing world system processes, especially when exposed to the public scrutiny by unexpected crises.
Internet is a physical and geographical network made of localized hardware and installed infrastructure. Cyber-spying conducted by intelligence agencies, and information warfare carried out by state or private hacker organizations, are operations increasingly adapted to the physical “outcrops” of the virtual battlefield.
The revelations on NSA spying immediately sparked generic privacy concerns among the public related to the free use of Internet services. Users started to complain about who actually benefited most from the digital interaction.
The problem has scaled up, and now the issue appears to be that the information backbone of the planet might be compromised by controlling strategies. The Internet infrastructure would be taken by intelligence applications well beyond its original neutral purposes and also out of range from ordinary countermeasures.
NSA has been accused of tapping directly into the Internet backbone connecting data centers. Private information access would not be only granted by the mediated access provided by major tech companies. The companies have adopted exceptional countermeasures based on cryptography to protect the traffic of data traveling between their centers.
Internet traffic, albeit distributed and fragmented by design, at large scales also shows a strong regional component due to the particular intercontinental connections of the network. In fact, NSA data centers access the raw Internet from specific US-based areas with respect to planetary data flows.
As an effect, that situation has singled out the digital operations in the North American and US territory as an “attention zone”, in the doubt that firms located there cannot be free of spying risks, since it is where US intelligence agencies directly access the gross Internet traffic.
This may undermine the confidence of worldwide investors in U.S. digital solutions, especially now that cloud computing is rising as a new paradigm, based on the remote use of computing resources of third-party storage and processing capabilities. Cloud computing companies based in U.S. have then to respond to localized Internet infrastructure issues, and security of transactions is considered a top priority.
The issue is combined with signs of skepticism for US networking technology, considering the possibility of the presence of NSA-devised cryptographic backdoors in otherwise secure hardware. US networking equipment may be seen unsuitable for the internal security policies of geopolitical contenders of US like China. For example, the decrease of Cisco’s sales of networking equipment in those markets has been traced back to this security issue by some analysts.
What emerges from those considerations is that the Internet is geographical and strictly bound to local physical infrastructure, making unsuitable the common top-down approach to it from safe and smoothly operating (but ineffective) virtual control rooms.
Methods employed by NSA exploit this fact and appear in line with a modern cyber-scenario where geolocation on the Internet is very important in determining the nature of any hacking threat, the related strategy of defense, and the geopolitical consequences of targeted attacks.
The “where” of the attacker has become as important as the degree of success in determining the long term consequences of the attack, defining the specific political outcomes and the responsibilities in the wider world context.
What seems just a glitch in the personal effectiveness of an Internet service suffering from unwanted information leaks, it is actually the result of large scale world operations contending the authority on the outcomes of future transactions.
Healthcare.gov is the recently introduced US federal e-commerce insurance website that has been at the center of a crucial and still unresolved technological discussion. The problems that plagued the registration and purchase process by end-users and intermediate agencies were indeed critical malfunctions in the operations of the website. The technical nature of the problem has quickly been linked to a major political debate and has been instrumental for contrasting political positions.
However, the planned service is not simply a standard e-commerce website but an effort to consolidate disparate databases about American citizens. Multiple public recording agencies are ambitiously linked to the complex back-office infrastructure of the insurance companies. The attempt is to combine multiple functions under a single inter-operating web-based hood.
Although the contribution of specialists to solving the technical problems has been much publicized, the nature of the issues has not been officially released nor it has leaked in any way. Judging from the news reports and the technologies involved, the major problem was represented by the required concurrent operations on the many agencies’ distributed databases, based in multiple geographical locations in systems with different or legacy software architectures and standards.
A series of technical glitches undermined the confidence in a politically relevant program, indicating that even an apparently doable sophistication in the digital infrastructure may not be at easy reach in the crucial public sector even in the era of widespread e-commerce use.
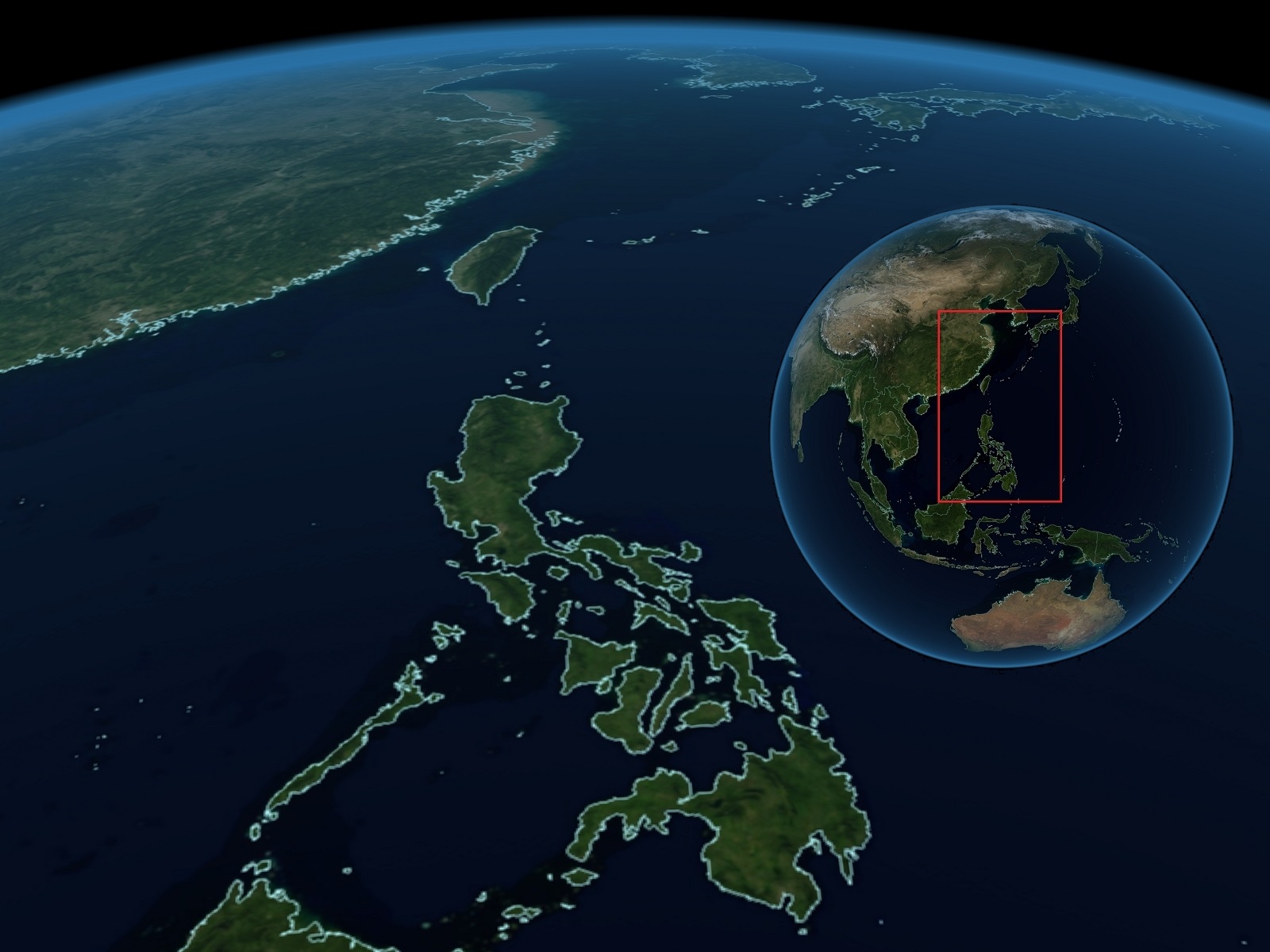 The Philippines and, in the center-background, the contested East China Sea. Satellite data from NASA’s Earth Observatory. Visualization by Marco Ruocco and MRU
The Philippines and, in the center-background, the contested East China Sea. Satellite data from NASA’s Earth Observatory. Visualization by Marco Ruocco and MRU
The rebuilding of critical infrastructure in the aftermath of the passage of typhoon Haiyan/Yolanda in the Philippines was a necessary step to support the humanitarian effort offered by many intervening countries. At the same time, it has been a good chance to induce change in the geopolitical balance of the region.
With the passage of Typhoon Haiyan the world community could witness the effects of the anomalous shutting down of all technological systems normally functioning in the areas along the track of the storm. An adequate response to the emergency could not count on any intermediate level of technological ability, since all technological systems were leveled by the weather event, including not only communications but also water distribution and road transportation.
The humanitarian response was thus based on local and international military intervention that was presented with the task of rebuilding from scratch all infrastructural services, from re-opening obstructed roads to building a new control tower in the airport in order to coordinate the local operations of incoming relief missions based on air transport.
The implication of the military intervention, that involved a U.S. aircraft carrier and other international military vessels, has been an increased activity in the vicinity of the disputed waters of the East China Sea, as all players involved could exploit the storm as a contextual diversion to attest advancement or consolidation of previous geopolitical positions.
Technical glitches have resulted in major consequences in the financial world. Twitter’s IPO has been carried out on the NYSE and not on the NASDAQ stock listing. The causes were probably the technical problems that characterized last year’s Facebook IPO, and which after that also affected some high frequency trading operations of the same exchange. In the end, the technology-oriented NASDAQ failed to attract a leading tech firm due to technical problems in its own technical management.
Last summer, a NASDAQ technical crash was caused by a faulty transmission of data between systems, in a period in which interchange standards for financial transaction are undergoing a necessary evolution. The process is similar to what can be seen in the open standards characterizing the geospatial data community.
Along the same lines, data centers are establishing themselves as crucial elements of the Internet backbone, but they are exposed to localized weather phenomena. In 2011 in Virginia an Amazon data center was hit by a storm that caused data loss and several hours of downtime for major Internet applications.
A well-visible feature on the website of Amazon Web Services (the leading cloud computing provider) allows to directly back up data geographically across the several data centers owned by AWS distributed around the world. The functionality reminds us of the precise geographical connotation of the Internet and makes geographical distribution a major variable to take into account in technological decisions.
A geospatial perspective is useful in the ongoing confrontation of daily business decision-making with a series of geographical variables, which determines the outcomes of world systems operations and shapes the overall geopolitical context. The provided examples suggest that it is better to avoid classifying geotechnology as yet another vertically-expert realm. Rather, it is worthwhile to consider it as a main variable of world systems functioning.
Technological crises also shed light on how closely bound are the world operations to geotechnology. Today it is advisable to improve the geospatial components of world systems more than operating on other, more traditional aspects, thus advocating the development of a dedicated community focused on those technological systems.